ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
MS.P.JENNIFER1, DR. A. MUTHU KUMARAVEL2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
The Security has become a main problem of concern among the people. Biometrics is robotic method of identifying a person based on physiological or behavioural uniqueness. Threat starts while an useless person tries to obtain access. A person verification system localizes facial landmarks and extracts biometrical features for face authentication. This includes image acquirement, segmentation, normalization, pattern generation and matching. Databases of biometrical facial appearance around the eye area of customers are constructing. The accuracy of the segmentation procedure plays a major role in the performance of the iris recognition system. Segmentation is performed by identifying the obligatory region from the acquired image. Image has to be smoothened to develop the accuracy. Noise present in the image is to be detached by using specific filter. This segmented image is to be normalized and Feature extraction takes place. The output of feature extraction will be in the form of bit template which will be compared to find for a match.
Keywords |
||||||||
| Biometrics systems, segmentation, normalization, feature extraction. | ||||||||
INTRODUCTION |
||||||||
| The use of biometric for identification purposes requires that a particular biometric factor be unique for each individual that it can be calculated, and that it is invariant over time. Biometrics such as signatures, photographs, fingerprints, voiceprints and retinal blood vessel patterns all have noteworthy drawbacks. Although signatures and photographs are cheap and easy to obtain and store, they are impossible to identify automatically with assurance, and are easily forged. Electronically recorded voiceprints are liable to changes in a person’s voice, and they can be counterfeit. Fingerprints or handprints require physical contact, and they also can be counterfeited and stained by artefacts. | ||||||||
| Human iris on the other hand as an internal organ of the eye and as well protected from the external environment, yet it is easily visible from within one meter of distance makes it a perfect biometric for an identification system with the ease of speed, reliability and automation. | ||||||||
| Recognition starts with acquiring the image and segmenting the iris and pupil by locating the centre of the eye and using concentric circles. The segmented image is normalized to remove the noise using Doughman’s rubber sheet model and undergoes feature extraction to generate the iris bit template and is compared using the hamming distance. | ||||||||
II. RELATED WORK |
||||||||
| There is associate degree ample quantity of connected add iris authentication system victimization numerous different techniques. Gorazd Vrček, Peter Peer [1] has conferred a System for private verification supported iris patterns. Iris is sometimes partly coated by eye lids and eyelashes. so as to scale back the false reject risk in such cases extra algorithms area unit required to spot the locations of eye lids and eyelashes, and exclude such bits within the ensuing bit templet. but this encountered miscalculation within the segmentation step, e.g. the segmentation of iris didn't succeed, and, consequently, unable to use additional steps. | ||||||||
| Kazuyuki Miyazawa, Koichi Ito, Takafumi Aoki, Koji Kobayashi associate degreed Hiroshi Nakajima[2] presents an algorithmic program for iris recognition victimization part-based image matching—an image matching technique victimization phase parts in 2nd discrete Fourier Transforms (DFTs) of given pictures. the employment of part parts of iris pictures makes it attainable to realize extremely correct iris recognition with an easy matching algorithmic program. so as to scale back the dimensions of iris information and to forestall the visibility of iris pictures, the concept of 2d Fourier part Code (FPC) for representing iris data is introduced. a serious drawback of this approach is that the 2nd FPC doesn't contain amplitude spectrum and also the actual iris image can not be reconstructed from the 2nd FPC. This causes issues within the “effective region extraction” stage and also the “displacement alignment” stage since these 2 stages ought to be performed within the abstraction image domain. | ||||||||
| Li Ma, Tieniu Tan, Senior Member, IEEE, Yunhong Wang, Member, IEEE, and Dexin Zhang [3] focuses on the last issue and describes a brand new theme for iris recognition from a picture sequence. the standard of every image within the input sequence and choose a transparent iris image from such a sequence for ensuant recognition is assessed. However, it got to be additional verified victimization real pictures. the quantity and also the category of iris samples employed in the experiments area unit of an inexpensive size. Therefore, the conclusions victimization the applied mathematics bootstrap technique supported such a knowledge set area unit helpful for each analysis and applications. | ||||||||
| S. P. Narote, A. S. Narote , L. M. Waghmare [4] presents the segmentation algorithmic program used for localization of iris for the event of strong iris recognition algorithms for biometric method. Iris localization plays a significant importance in iris identification. the tactic determines an automatic threshold for binarising and determines the pupil center supported a bar chart of grey scale image. enforced algorithmic program could be a simple automatic segmentation algorithmic program for extracting iris from the image. Provides associate degree adequate and acceptable accuracy. but suffers from pitfalls just like the lid and eyelashes artifacts don't seem to be thought of, that degrades the performance of the iris recognition system. | ||||||||
| Sepehr Attarchi, Karim Faez, Amin Asghari [5] mentioned a completely unique technique for iris segmentation employing a advanced mapping procedure and best-fitting line within the new advanced domain is conferred. Associate degree intensity threshold technique with cagy edge detector to extract the rough region of the pupil. Actual inner and outer boundaries of the iris were found by remapping the best-fitting lines to original domain. Lower a part of the iris was employed in the popularity approach. Smart results achieved employing a advanced mapping procedure and best-fitting line within the new advanced domain. | ||||||||
| Ghassan J. Mohammed, Hong BinRong, and Ann A. Al-Kazzaz Maan Younis Abdullah[6] planned associate degree economical iris localization technique supported the angular integral projection perform (AIPF) to discover the iris boundaries in iris pictures. The algorithmic program adopts boundary points detection and curve fitting. First, the approximate pupil center is obtained. Then, 2 sets of radial boundary point’s area unit detected for the iris inner and outer boundaries victimization AIPF technique. This algorithmic program adopts boundary points detection with curve fitting and it doesn't got to realize all the boundary points, thus its localization speed is extremely quick. | ||||||||
| Belhassen Akrout, Imen Khanfir Kallel, Chokri mountainamar and Boulbaba Ben Cupid [7] planned Signature extraction for iris authentication is predicated on gray level bar chart to extract the pupil, the second is predicated on elliptic and parabolic HOUGH transformation to determinate the sting of iris, higher and lower eyelids, the third is 2nd physicist Wavelets to cipher the iris and eventually used the playing distance for authentication. but the angle of capture of the attention depends on the position and also the degree of rotation on the pinnacle what poses issues of authentication albeit the compared irises belong to a similar eye.The current use of the technology of authentication containing iris is restricted as a result of it's high-priced. | ||||||||
| Makram Nabti, Ahmed Bouridane [8] proposal uses a multi-scale edge detection victimization wave maxima for iris localization followed by a physicist filter bank decomposition for feature extraction whereas matching is disbursed by computing the playing codes of various irises. planned algorithms area unit effective and sturdy. The results obtained clearly show that the system is reliable, secure and might be simply enforced at essential places for the identification of persons by their irises. the present technique therefore achieves higher accuracy. but less stress on multimodality of the system. | ||||||||
| Padma Polash Paul, Md. Maruf Monwar [9] has mentioned that the iris recognition system consists of associate degree automatic segmentation, standardization. Finally, the part information from 1D Log-Gabor filters was extracted and quantity to four levels to cipher the distinctive pattern of the iris into a bit-wise biometric templet. The playing distance was used for classification of iris templates It works well once tested victimization 2 databases of grayscale eye pictures so as to verify the claimed performance of iris recognition technology. The encryption method solely needed one 1D Log-Gabor filter to produce correct recognition. | ||||||||
| K. Masood, Dr M. Y. Javed and A. Basit [10] planned associate degree economical localization technique is conferred to spot pupil and iris boundaries victimization bar chart of the iris image. 2 tiny parts of iris are used for polar transformation to scale back procedure time and to extend the potency of the system. wave rework is employed for feature vector generation. Rotation of iris is remunerated while not shifts within the iris code. bar chart primarily based technique has been planned for iris localization. | ||||||||
III. PROBLEM STATEMENT |
||||||||
| This paper proposes a mechanism to scale back the value and improves segmentation by making certain the performance. The aim of this new approach is to form the system wide used. the present systems area unit pricey so it’s used solely in necessary places like international airports. | ||||||||
IV. METHOD FLOW |
||||||||
| Authentication system captures the face in real time and identifies the attention region when that the attention half is divided from the face image. This divided image performs iris localization. This output is normalized then undergoes unwrapping and encryption. This result's compared with the iris within the information if match found the person is documented else not a licensed person and doesn't demonstrate. | ||||||||
4.1 IMAGE ACQUISITION |
||||||||
| Image is captured using digital camera and is transferred to the file for processing. Image undergoes preprocessing. From the acquired image, region required for processing is identified. K-means clustering algorithm is used to identify the region.The Eucledian distance metric is given by | ||||||||
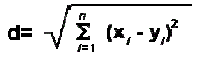 |
||||||||
| where d represents the distance and x,y represents the points.This gives the distance between the x and y co-ordinate of points and n represents the number of points. In the algorithm squared Euclidean distance metrics is used. This is same as Euclidean but does not involve the square root. This is summation of the square of the difference between the x and y co-ordinate of the points. | ||||||||
4.2 SEGMENTATION |
||||||||
| Once the region is identified the image is to be divided into quadrants to segment eye alone. Then the task consists of localizing the inner and outer boundaries of the iris. Both are circular, but the problem lies in the fact that they are not cocentric. The two circles must be evaluated separately. After identifying the pupil with this centre concentric circles are drawn till a change in intensity is identified. This final circle gives the outer boundary that is iris. | ||||||||
4.3 NORMALIZATION |
||||||||
| Two images of the same iris might be very different as a result of i) size of the image. ii)Size of the pupil. iii) Orientation of the iris.To cope with this, the image is normalized by converting from Cartesian to doubly dimensionless polar reference form as shown below | ||||||||
4.4 ENCODING AND MATCHING |
||||||||
| Generate a template code along with a mask code. Compare the two iris templates using Hamming distances. Gabor filters are used for encoding and Hamming distance for matching.Shifting of Hamming distances takes place to counter rotational inconsistencies and if it is less than threshold value Iris match found if it is greater than the threshold value no match with the iris in the database. | ||||||||
V. RESULT AND DISCUSSION |
||||||||
| MATLAB is an interactive environment and high-level language that enables to perform computationally intensive tasks faster than with traditional programming languages such as C, C++, and FORTRAN. This also includes Graphical User Interface. MATLAB supports structure data types. Since all variables in MATLAB are arrays, a more adequate name is "structure array", where each element of the array has the same field names. MATLAB supports elements of lambda-calculus by introducing function handles, or function references, which are implemented either in .m files or anonymous/nested functions. | ||||||||
| The authentication system is accessed through a Graphical User Interface. This is given as input form which allows the user to select the option to perform. The operation gets the image from the database performs region identification and as a result gives the identified region from the image selected. | ||||||||
| This undergoes segmentation and is normalized. The polar co-ordinates are used for generating bit templates and is compared with the threshold value. Good results are achieved. | ||||||||
VI. CONCLUSION |
||||||||
| This paper has presented a heuristic approach based on the segmentation algorithm and reducing the cost by using the digital cameras. This ensures the performance by increasing the speed in the clustering which is used to identify the eye region. The set of images placed in the file is used for identifying the required region which in turn highlights the white region of the image and other regions are made black. This works for monochrome and also color images. The images in the file are captured in a standard posture. | ||||||||
Figures at a glance |
||||||||
| ||||||||
|
||||||||