ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Paramjit Shah Singh1, Ajay Kumar Agarwal2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
There are many countermeasure methods that have been extensively studied to provide WSN communication security. However, WSN is still exposed to some kinds of attacks. These defenses are ineffective against attacks from compromised servers due to the WSN level constantly increasing, and attacks are becoming more and more complicated. Moreover WSN has some restrictions when it comes to its applications, like limited power supplies, low bandwidth, small memory sizes and limited energy, which make it more vulnerable.To this end, we propose a security algorithm keeping in mind the constraints of WSN. We have modified the Feistel algorithm by using controlled permutation boxes. The modified Feistel scheme design can meet today’s security challenges and generates high-quality results.
INTRODUCTION |
| Due to the increase in new trends of attack, previous security methods cannot combat or resist modern attacks. Analysis of work done in the field of encryption, shows that new and more stable security approaches need to be put in place to provide information safety taking into consideration the following attributes: availability, confidentiality, integrity authentication, and non-repudiation.On designing WSN protocol it is necessary to consider all specific features of WSN. For example, communication bandwidth is extremely limited in these networks: each bit transmitted consumes about as much power as executing 800~1000 operational instructions, and as a consequence, any message expansion caused by security mechanisms comes at a significant cost.Limitations in computational and battery power in sensor nodes are constraints on the diversity of security mechanisms. We must apply only suitable mechanisms to WSN which motivates development of efficient encryption scheme. Our work is an endeavor to develop such cipher to provide efficient security for sensor nodes. This accelerated-cipher design uses Feistel scheme with data-dependent permutations and more secure building blocks , and can be used for fast hardware, firmware, software and WSN encryption systems. The approach presented here is less likely to suffer, intrusion of differential cryptanalysis than currently used popular WSN ciphers like DES, Camellia and so on. |
II. LITERATURE REVIEW |
| Block ciphers were developed in nineteen seventies and have been used to encrypt loads of valuable information while it is either stored or is in transit through network. Modern block ciphers have got a lot of strength through the work of Claude who introduced the idea of substitution-permutation (S-P) networks which form the basis of modern block ciphers. S-P networks are based on the two primitive cryptographic operations Substitution and Permutation. To provide more security to a cipher[1] it may make use of both substitution as well as permutation that to several times (combinations). The work of Kelleher, L.; Meijer showed that use of S-P network can protect against linear as well as differential attacks.[2][3]. |
| Horst Feistel led to the invention of a suitable structure which adapted Shannon's S-P network in an easily inverted structure. Essentially the same h/w or s/w is used for both encryption and decryption, with just a slight change in how the keys are used. It involves use of several key dependent rounds, involving a round function which involves use of substitution and permutation. The idea is to partition the input block into two halves, L(i-1) and R(i-1), and use only R(i-1) in the ith round (part) of the cipher the function in each round, incorporates one stage of the S-P network, controlled by part of the key K(i)known as the ithsubkey [4].In 1999 NIST announced the five algorithms : MARS[12], RC6[13], Rijndael[14], Serpent[15], and Twofish[16]. MARS breaks the 128-bit input block into four 32-bit words. MARS uses a 32-round unbalanced Feistel network. RC6, a 20-round Feistel cipher out of RSA Security Inc., is much simpler. “Pre-whitening” and “Post whitening” steps have been used to increase the strength of algorithm. Twofish, is a 16- round Feistel network with two modifications. One is a one-bit rotation before and after the data enters the round function. The other alteration is dynamic S-boxes. In serpent ,there are 32 rounds—a high number—each of which consists of XORing the key and the intermediate data, a pass through Sboxes, and a linear function that combines fixed rotations and XOR. Bruce Scheneir[17] proposed a fast and unpatented block cipher available freely to people for public use. Blowfish[18] is a secret-key block cipher, is a Feistel network, iterating a simple encryption function 16 times. The block size is 64 bits, and the key can be any length up to 448 bits. |
III. PROPOSED ALGORITHM |
The Encryption Process |
| First of all, given plaintext message is divided into blocks of 128 bits (or 16 characters).If the length of plaintext message is l and no. of plaintext blocks in this length are ‘n’ and if l < n*16, then original plaintext message is augmented with padding of blank spaces so that last block should also be of 16 characters (128 bits). |
| Each of the blocks of plaintext message is encrypted to produce final block of ciphertext. |
Detailed Architecture of Encryption Process |
Encryption algorithm: |
| 1. Plaintext of 128 bits is XORED with first intermediate key K1 of 128 bits. |
| 2. The output of 128 bits is considered as consisting of two independent 64 bits left half (L0) & 64 bits right half (R0). |
| 3. L0-R0 is passed through main function (F). |
| 4. The output of main function is |
| LO’=R0 |
| RO’=L0 |
| 5. LO’-RO’ is then passed through sub function which acts like a wrapper layer to strengthen the other half (RO’) using 128 bits key K3. |
| 6. 128 bits output of sub function is then passed through main function (F). |
| 7. Repeat steps 2-5 using intermediate keys K4 & K5 in main functions & sub main function. |
| 8. 128 bits output of sub function is then passed through main function (F). |
| 9. Repeat step 4 using intermediate keys K6. |
| 10. 128 bits output is XORED with 128 bits intermediate key K7 to generate 128 bits output. The detailed architecture of encryption process is shown below : |
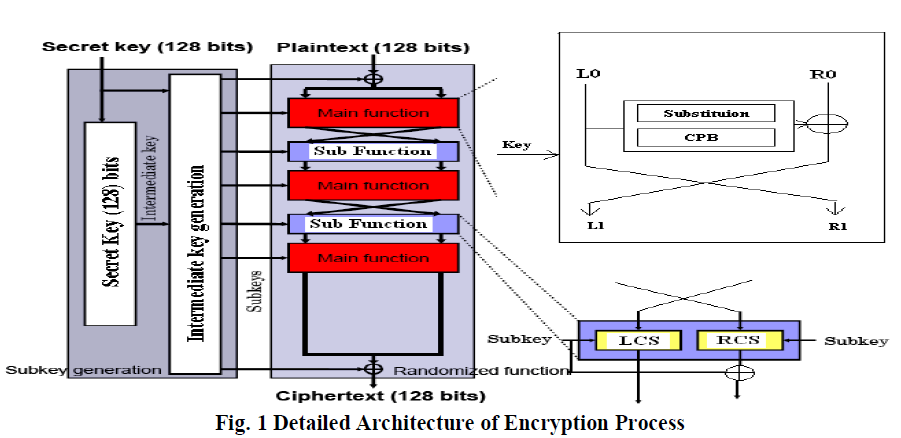 |
The encryption process consist of following segments : |
| 1. Generation of intermediate keys |
| 2. Application of Main function |
| 3. Application of Sub function |
| Alongwith this key whitening is used to ensure resistance against key search attack. |
| In intermediate key generation, from main key of 128 bits main keys and sub keys are derived. |
| The top and bottom rounds of the cipher play a different role than the middle rounds in protecting against cryptanalytical attacks. |
| Therefore, in the design of this cipher the middle rounds are viewed as the “cryptographic core” and are designed differently than the top and bottom rounds, which are viewed as “wrapper layers”. |
A. Intermediate Key Generation |
| New intermediate key is produced from existing key using followingalgorithms: |
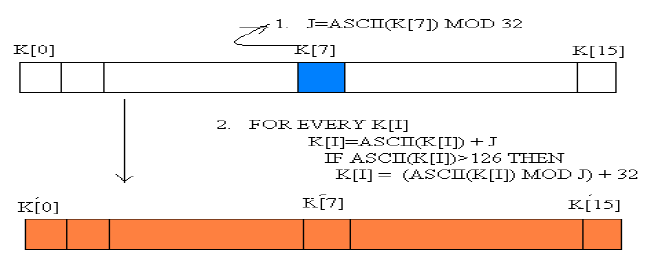 |
B. Main Function |
| The main function is the cryptographic core, which plays very important role in ensuring the security of the data. It performs substitution on left half of the input i.e. leftmost 64 bits, it produces pre-purmuted output which is passed through CPB, which dynamically generated the permutation box which helps in rearranging the pre-purmuted output to produce the permuted output. The block diagram of Main Function is shown below : |
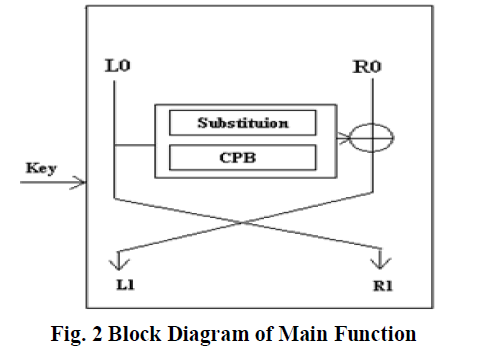 |
C. Sub-Main Function |
| This plays very important role, as it tightens the security further. This heterogeneous structure of Feistel cipher is far more secure than standard Feistel cipher where each step is just similar to previous one, hence is less resilient to attacks being predictive in nature. Output of main function is passed through the sub main function where shifting operation is performed using sub keys, ensuring better diffusion. |
| The block diagram of Sub Main Function is shown below: |
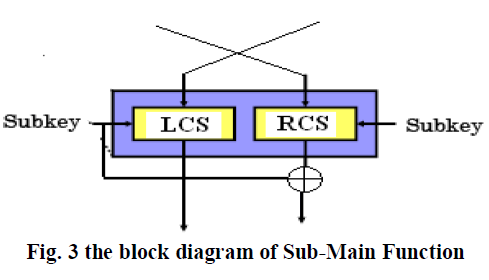 |
D. Substitution |
| • In principle, a carefully chosen substitution can provide good resistance against linear and differential attacks, as well as good avalanche of data and key bits. |
| • A drawback of using S-box lookups is that it is relatively slow for software implementations and in order to use all the bits of a data word, one needs to do several S-box lookups, which slows the cipher even further. |
| • Therefore, direct substitution is performed rather than large number of S-box lookups. This approach prevents memory wastage and exhaustive computations. |
| The block diagram of Substitution is shown below: |
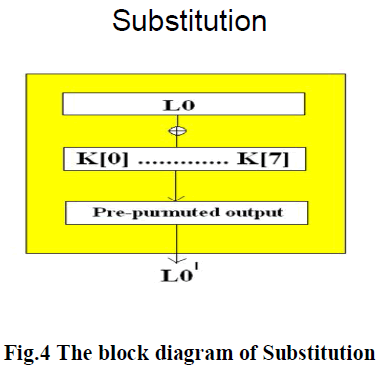 |
Steps of Substitution Algorithm |
| 1. 64 left most bits (L0) is XORED with 64 bits of intermediate key i.e. |
| oi = LOi |
| LOi = ith binary digit of plaintext |
| ki = ith binary digit of key |
| oi = ith binary digit of output |
E. CPB-Controllable Permutation Box |
| • Key-dependent, pseudo-randomly generated controllable permutation boxes (CPB) are used. |
| • Traditional systems, however, uses the cryptosystem itself to generate the P-boxes, which Produces weak PBoxes – here this approach is avoided. |
| • Key dependent pseudo randomly generated CPB is used which is created at runtime only using the secret key, which is more secure than static P-Box. |
| • Permutation operation rearranges the contents and adds to diffusion in the given contents but if static permutation tables are used, they get easily attacked than when CPB based key dependent permutations are used. |
| • CPB are fast even if implemented in cheap hardware or limited resource devices. |
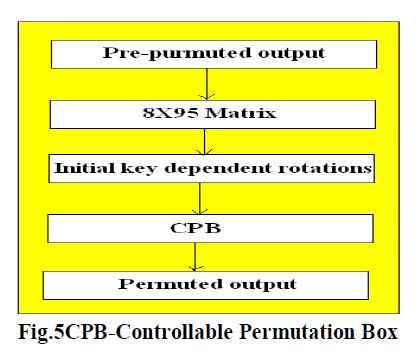 |
 |
CPB-Controllable Permutation Box-Generation |
| 1. The ith row of the matrix is rotated k[i+1] times |
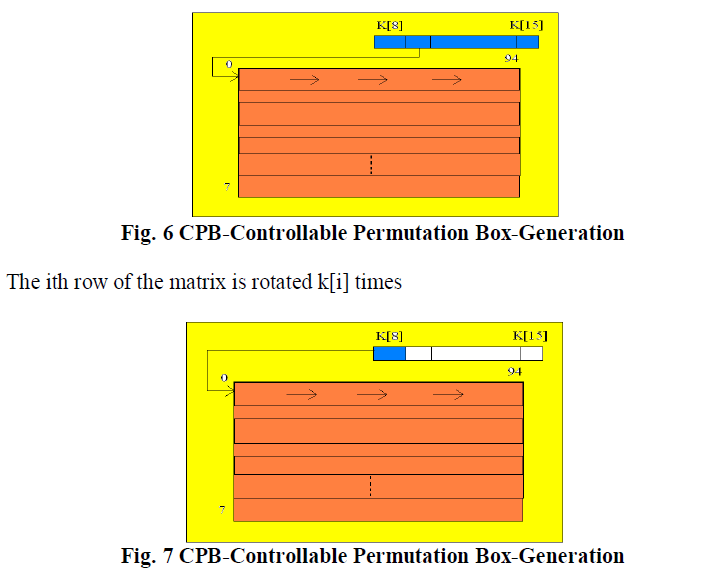 |
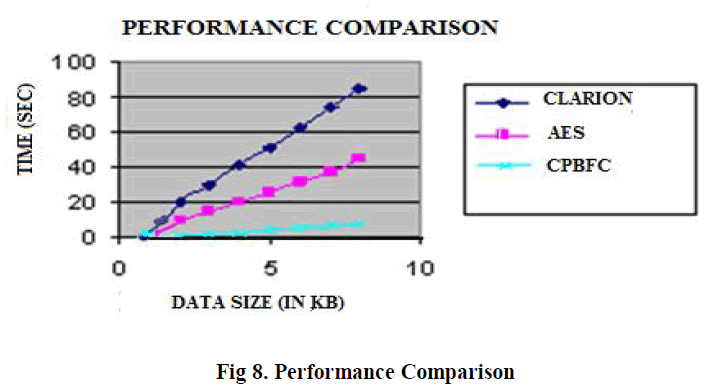
IV. PERFORMANCE COMPARISON OF PROPOSED ALGORITHM |
| By considering different sizes of data blocks the algorithms are evaluated in terms of the time required to encrypt and decrypt the data block. The time between two test points in the algorithm during execution is calculated using system clock. The number of bytes encrypted in one second is ascertained. |
| The comparison between proposed algorithm (CPB-FEISTEL CIPHER) with standard algorithms given below reveals the fact that proposed algorithm, performs better than other algorithms. |
 |